Router Network Map Tool
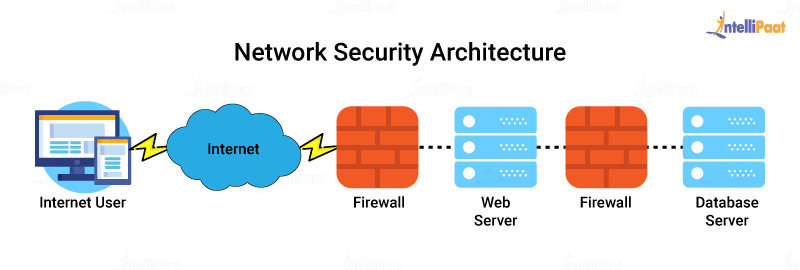
If you are managing a home or office network, a router network map tool can be an invaluable asset to help visualize, monitor and diagnose network connectivity issues. It enables you to get a complete view of your network, understand connectivity pathways and see what devices are connected to your network.
Router network map tools create a visual representation of your network that allows you to easily comprehend the complexity of your network infrastructure. This tool helps to visualize your network in real-time with information such as the IP address of your devices, how they are connected and which devices are causing disruptions. With this tool, you'll be able to scan your network for any potential problems, identify which devices are using up the most bandwidth, and control the devices that are connected to your network.
The router network map tool is highly beneficial for proper network management, simplifying troubleshooting processes, and improving network performance by decreasing response times.
In summary, a router network map tool is an essential tool for network administrators and tech-savvy individuals alike. It empowers them to visualize their network infrastructure and improve network performance. With the router network map tool, you can easily monitor, diagnose and manage your network from anywhere with an internet connection. Try it out for yourself, and see just how much it can transform your network administration experience.