Router security features
Router Security Features
As the number of internet users continues to grow, cyber attacks, data breaches, and other online security threats have become increasingly common. One of the best ways to protect your network and devices is by using a secure router. Routers come with a variety of security features that can help safeguard your network against digital threats. In this article, we will discuss some of the essential security features to looks for in a router.
Firewall
A firewall is the first line of defense against internet threats. It acts as a barrier between your network and the internet, regulating incoming and outgoing traffic. A router with a built-in firewall ensures that only authorized traffic can enter your network, blocking any unauthorized access.
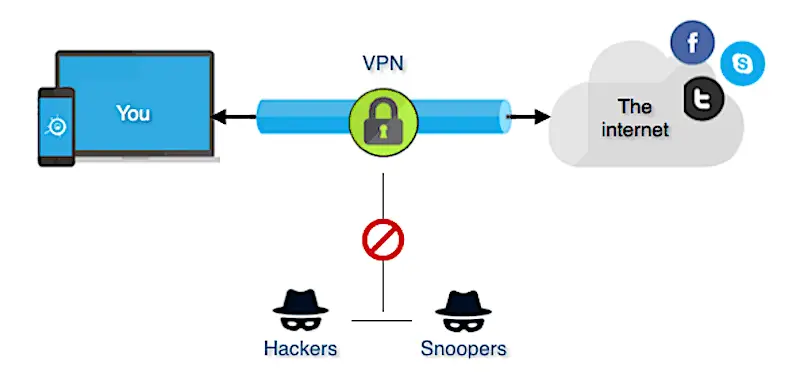
Virtual Private Network (VPN)
A VPN lets you create a secure connection to a remote network or device. With a VPN, you can access data on an office or home network from anywhere in the world. It also encrypts your data and protects your privacy. A router with a VPN feature lets you connect all your devices to a secure network.
Wireless Encryption
Wireless encryption is a crucial security feature that encrypts data transmitted over the wireless network. Without it, anyone nearby with a wireless device can potentially eavesdrop on your network traffic. The most common wireless encryption protocols are WPA (Wi-Fi Protected Access) and WPA2.
Guest Network
A guest network allows your guests to access the internet without accessing your private network. It separates the network traffic, ensuring that your guests cannot access your files and sensitive data. A router with a guest network feature is ideal if you have frequent visitors to your home or office.
In conclusion, a secure router is an essential component of your home or office network. By choosing a router with the above security features, you can improve the security of your network and protect against digital threats.