When it comes to running a business, network performance optimization is a vital factor that needs to be considered. In today's digital world, companies rely heavily on their networks to carry out their daily operations. A slow or inadequate network can adversely affect the company's productivity and profitability. Therefore, it is crucial to ensure that the network is optimized for peak performance.
The optimization of network performance involves several factors, including the use of the right hardware and software, proper network architecture, network security, and adequate bandwidth. These elements work together to ensure that the network is reliable, secure, and meets the needs of the users.
Bandwidth management is one of the critical factors involved in network performance optimization. High bandwidth utilization can lead to network congestion and negatively impact network performance. Therefore, it is essential to manage bandwidth effectively by prioritizing essential applications and limiting unnecessary bandwidth usage.
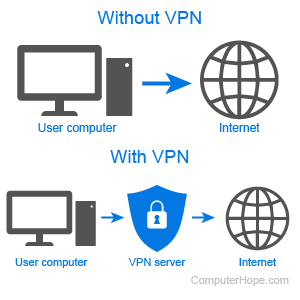
Another aspect of network performance optimization is network security. Cyber threats are rampant in today's digital world, and a security breach can be costly for businesses. Therefore, it is crucial to ensure that the network is protected from cyber threats by implementing robust security measures such as firewalls, antivirus software, and intrusion prevention systems.
In conclusion, optimizing network performance is a necessity for business success in today's digital world. It involves multiple factors such as hardware and software, network architecture, bandwidth management, and network security. By taking the necessary steps to optimize network performance, businesses can ensure reliable and secure network infrastructure that enables them to focus on their core operations.