Network Traffic Simulator Tool: Optimize Your Network Performance
Are you looking for a way to test your network performance and ensure that everything is functioning as it should? If so, then a network traffic simulator tool might be just what you need.
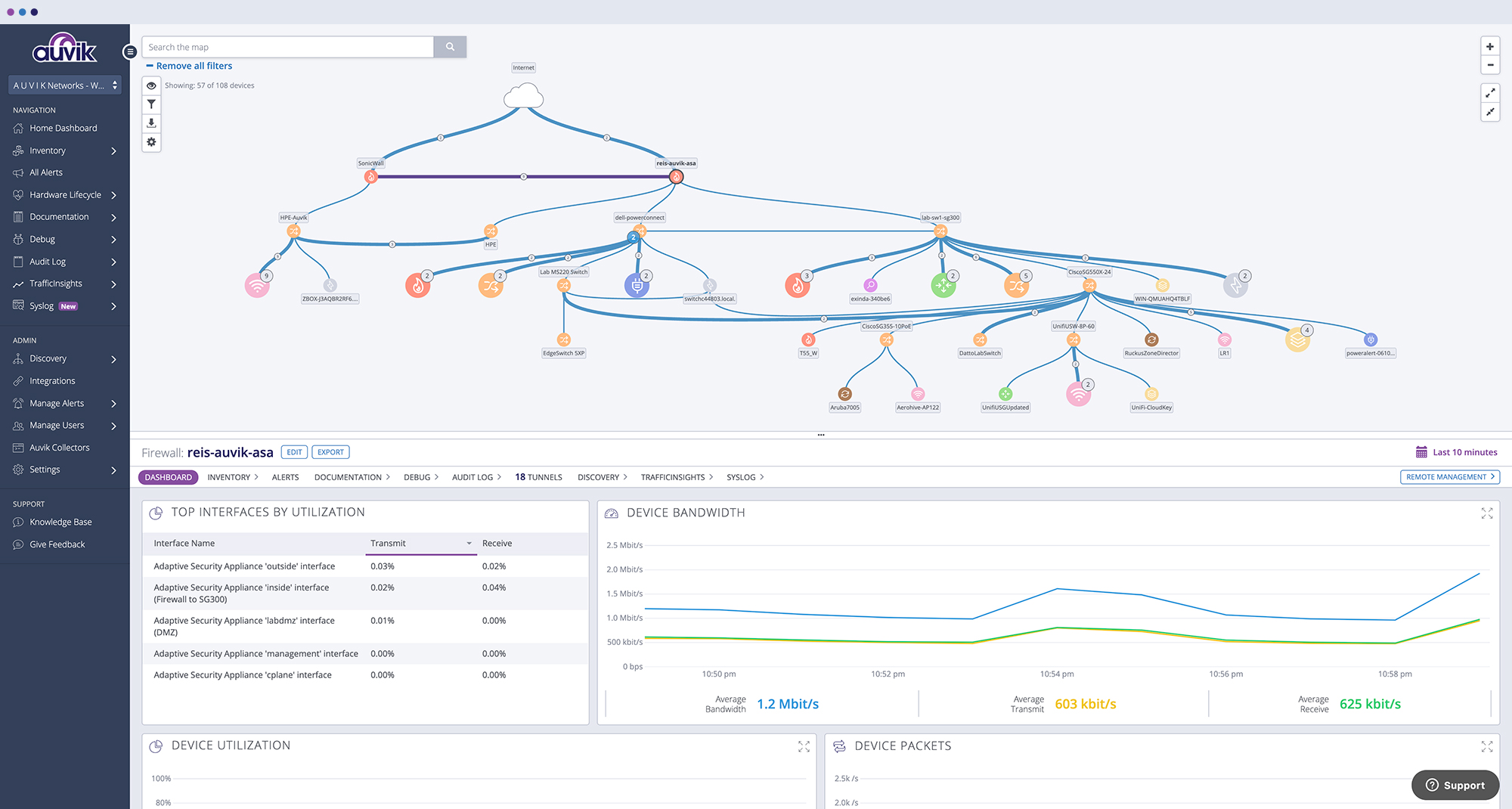
A network traffic simulator tool is software that can simulate different types of network traffic to test the capabilities of your network infrastructure. With this tool, you can run simulations to analyze how your network would perform under different conditions, such as heavy traffic, high amounts of data transfer, and latency.
The benefit of using a network traffic simulator is that it allows you to identify potential bottlenecks or issues before they become critical. By identifying these problems early, you can take action to optimize your network performance for better efficiency and speed.
One popular example of a network traffic simulator tool is the Cisco Packet Tracer. This tool enables you to simulate a variety of network types, including LAN, WAN, and WLAN. You can create different scenarios, test various protocols, and analyze how your network would perform in a real-world environment.
Another network traffic simulator tool is the Open Source Network Emulator (OPEN), which can simulate different types of networks, applications, and network protocols. This tool allows you to analyze how your applications would perform in different network environments, giving you a better understanding of how to optimize your network infrastructure.
In conclusion, using a network traffic simulator tool is an effective way to optimize your network performance, identify potential issues, and improve efficiency. Whether you choose a commercial or open-source option, using a traffic simulator tool can give you peace of mind and confidence in your network's capabilities.