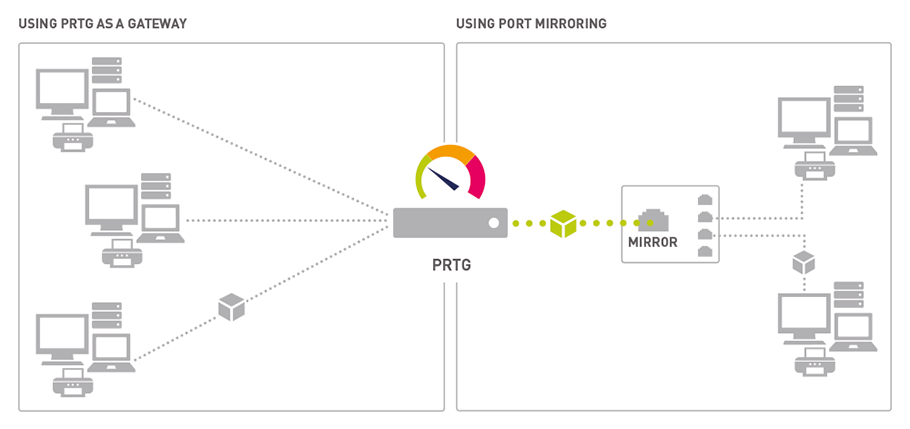
If you're concerned about the security of your router, you're not alone. As our homes become more interconnected thanks to Internet of Things (IoT) devices, the humble router has become a crucial piece of hardware that needs to be secured. Luckily, there are several router security software solutions available to safeguard your network.
Firewalls
A firewall is an essential piece of router security software. It works by monitoring incoming and outgoing network traffic to block unauthorized access to your network. Some routers come with built-in firewalls, while others require you to install a third-party firewall software.
Antivirus and Anti-malware Software
Antivirus and anti-malware software are essential for protecting your network against viruses and malware. They scan your network for any suspicious activity and detect and remove any malicious software on your devices.
VPN Software
A VPN or Virtual Private Network encrypts your internet connection to keep your data safe, no matter where you're connected. VPN software is commonly used to secure your internet connection when accessing public Wi-Fi networks.
Parental Control Software
Parental control software is useful if you have children who use the internet. It allows you to set filtering and blocking of content, limit internet access during certain times of the day, and monitor your child's online activity.
Password Management Software
A password manager is an essential piece of software if you have trouble remembering passwords. It stores your passwords securely and generates complex passwords for you. This means you don't have to reuse passwords, making your network more secure.
In conclusion, securing your home router is vital in today's interconnected world. By installing router security software, you can safeguard your network from cyber threats and protect your privacy online.