Router QoS Configuration: Prioritizing Your Network Traffic
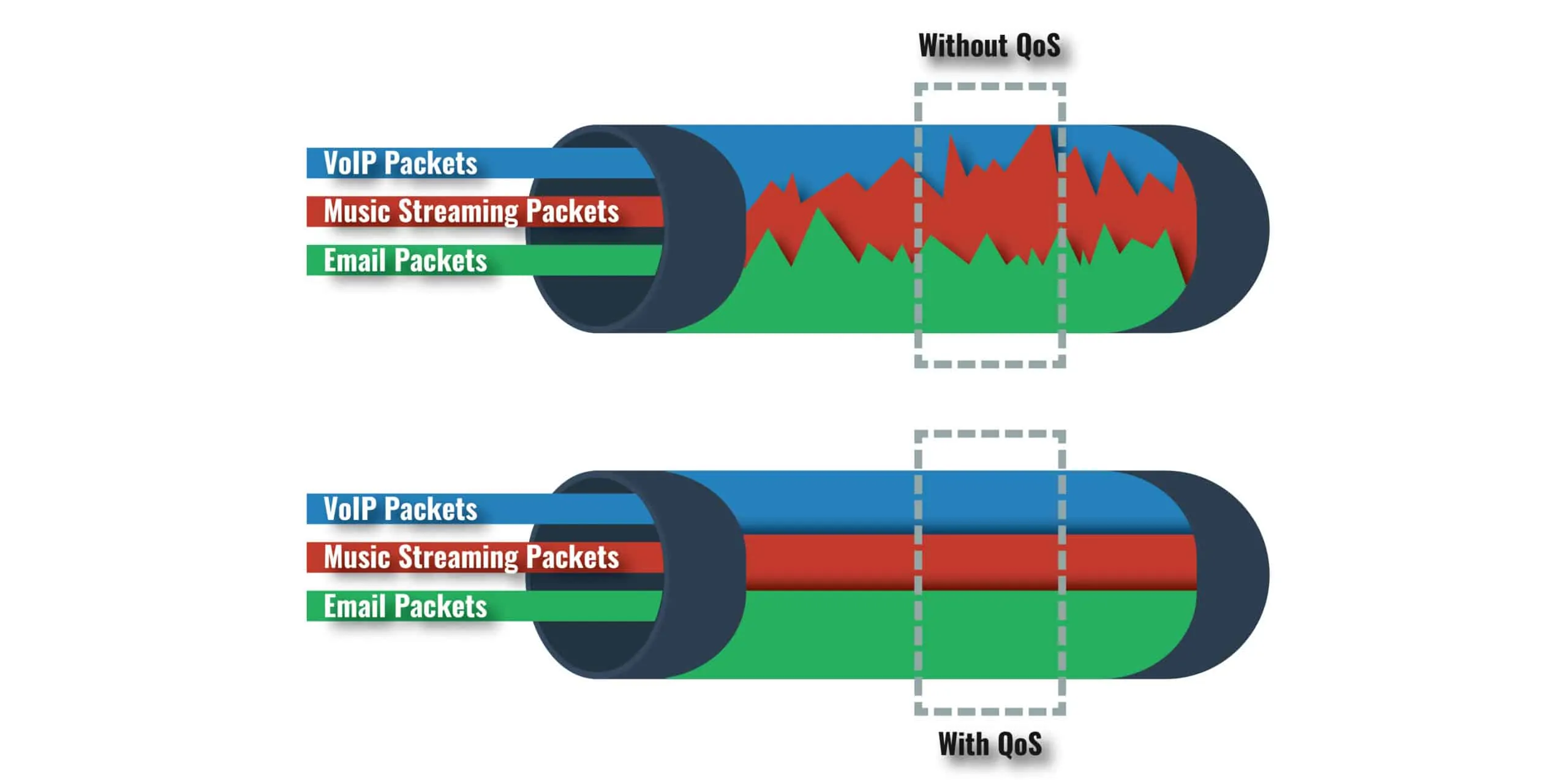
As internet usage expands, the need for routers that can prioritize traffic has become essential. QoS or Quality of Service is a router feature that enables it to manage network traffic efficiently. With QoS, you can set priorities for specific applications or devices and streamline the flow of data throughout your network. In this article, we will discuss how you can configure QoS on your router and ensure your apps and devices receive fast, reliable connectivity.
Step 1: Understanding the Traffic
Analyze your network traffic patterns and identify which devices and applications require the most bandwidth. Some apps and devices, such as streaming services, video calls or gaming systems, require higher bandwidth and lower latency than other devices or applications.
Step 2: Enabling QoS
Most modern routers come with QoS pre-installed. To enable QoS on your router, go to the router settings page and look for the QoS settings. Enable the QoS feature and select the type of QoS profile that works best for your network.
Step 3: Prioritizing Your Traffic
Once you have enabled QoS, prioritize your network traffic. You can do this by assigning high priority to the devices or applications that require the most bandwidth. Alternatively, you can assign low priority to devices or applications that require less bandwidth, such as emails or web browsing activities.
Step 4: Testing Your Network
After configuring your router's QoS settings, you should test your network to ensure that it's optimized. Run a speed test to determine how your network performs compared to your service provider's advertised speeds. If you notice any issues, readjust your QoS settings, and test again to find the optimal settings for your network.
In summary, QoS configuration is an essential feature that ensures the efficient utilization of your network resources. By analyzing your traffic patterns, enabling QoS, prioritizing traffic, and testing your network, you can ensure that your network devices and applications receive fast, reliable connectivity.