In today's world, where we depend on the internet for almost everything, a problem in our router or WiFi can be frustrating. It can slow down our work, hinder our entertainment or cause miscommunication in our household. However, router and WiFi troubleshooting can be done on our own without the need for a technician, provided we know what to look for.
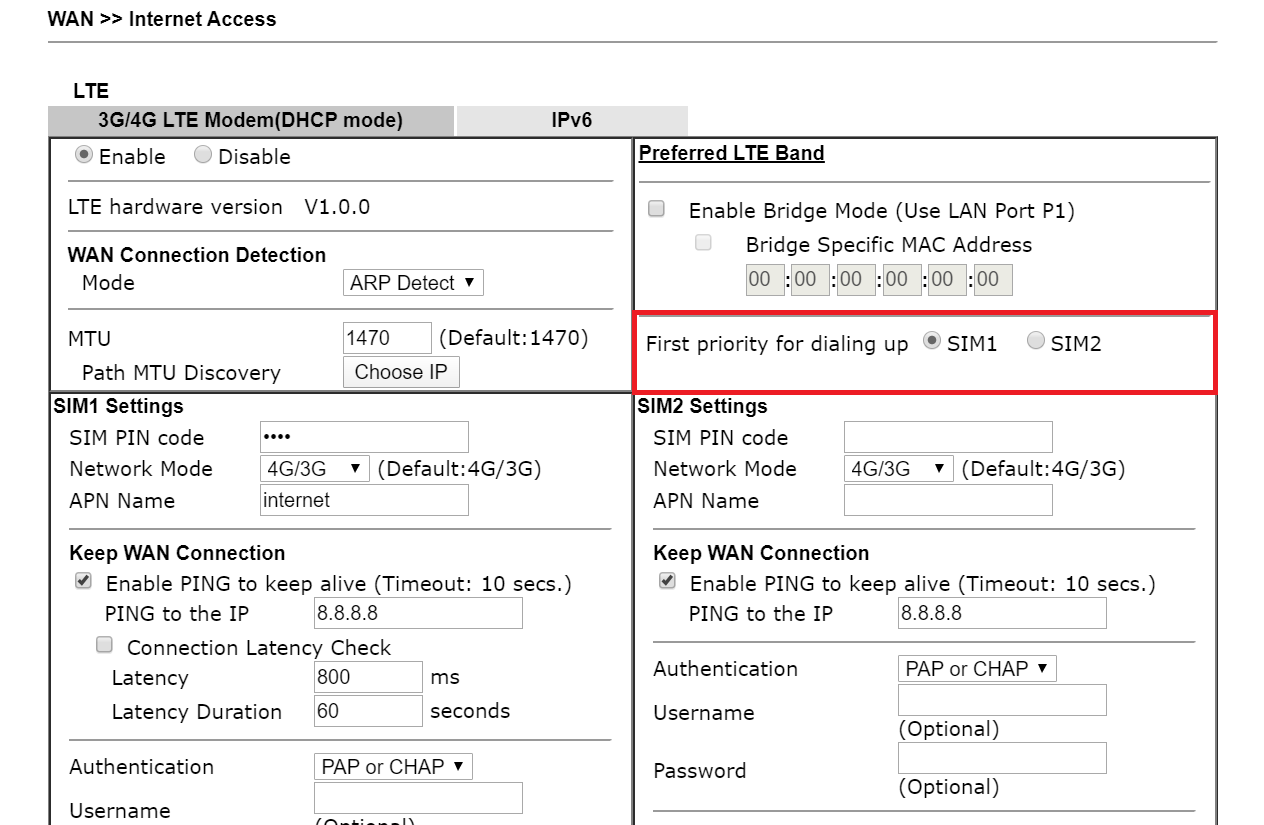
Router Troubleshooting:
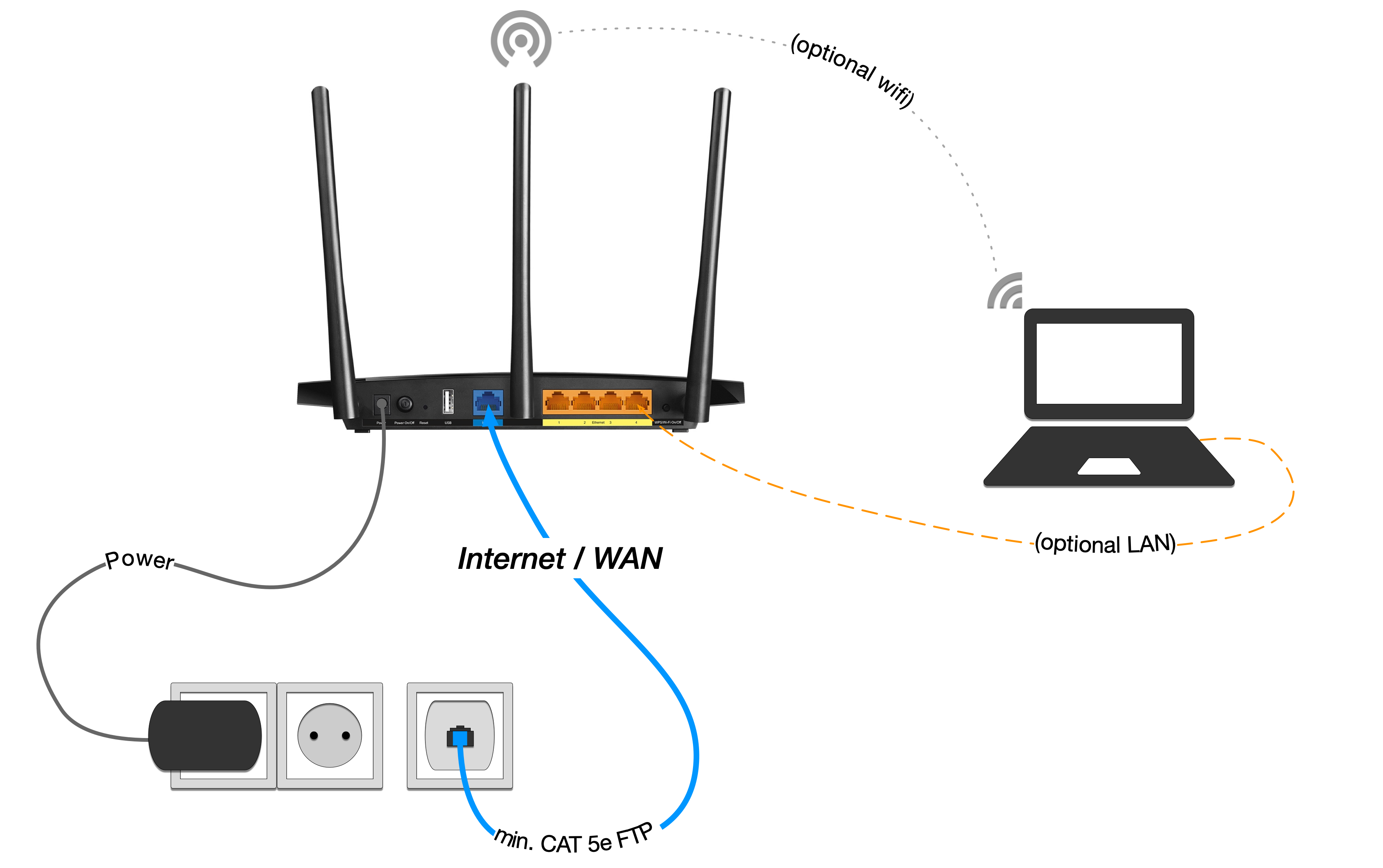
- Ensure that the router is turned on and plugged in properly to the power outlet.
- Check for any loose or disconnected cables between the modem and the router.
- Update the firmware of the router to get the latest feature updates and bug fixes.
- Reset the router to its default settings if the issue still persists.
WiFi Troubleshooting:
- Check if other devices are connected to the WiFi and if they are experiencing the same issue.
- Verify if the WiFi is turned on and if the SSID and password are entered correctly on the device.
- Move the device closer to the WiFi router to see if connectivity improves.
- Reduce interference due to other electronic devices or household objects by changing the channel on the router.
One can also try turning the router and modem off for a few minutes and restarting them, which sometimes helps in solving minor issues. If the issue persists, we can always contact the customer service representative for further assistance or consider purchasing a new router or modem.
Router and WiFi troubleshooting may seem intimidating, but maintaining a smooth internet connection is essential for uninterrupted work, entertainment, and communication. A few quick fixes can save us from unnecessary headaches and improve our overall internet experience.