Network Modem Configuration
If you want to connect to the internet, you'll need a modem to do so. A modem is a device that connects your computer or other devices to the internet via a network connection. However, in order for your modem to work properly, it needs to be configured correctly.
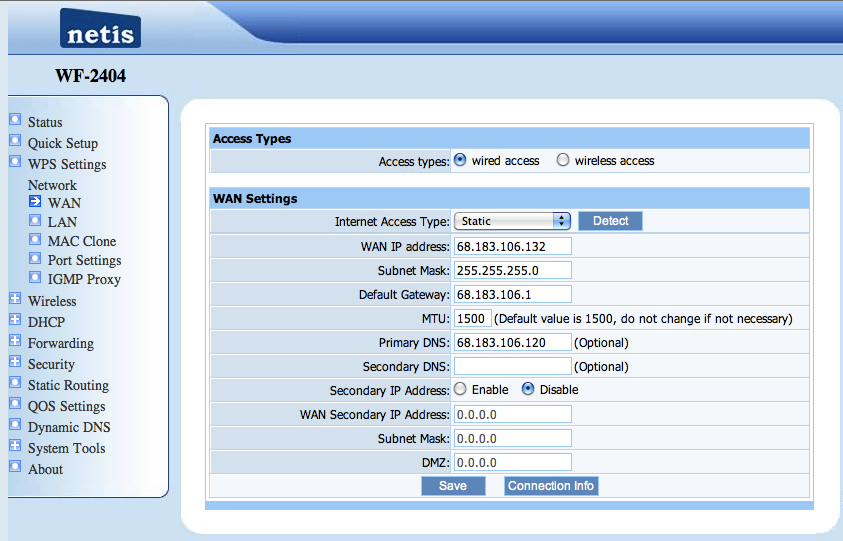
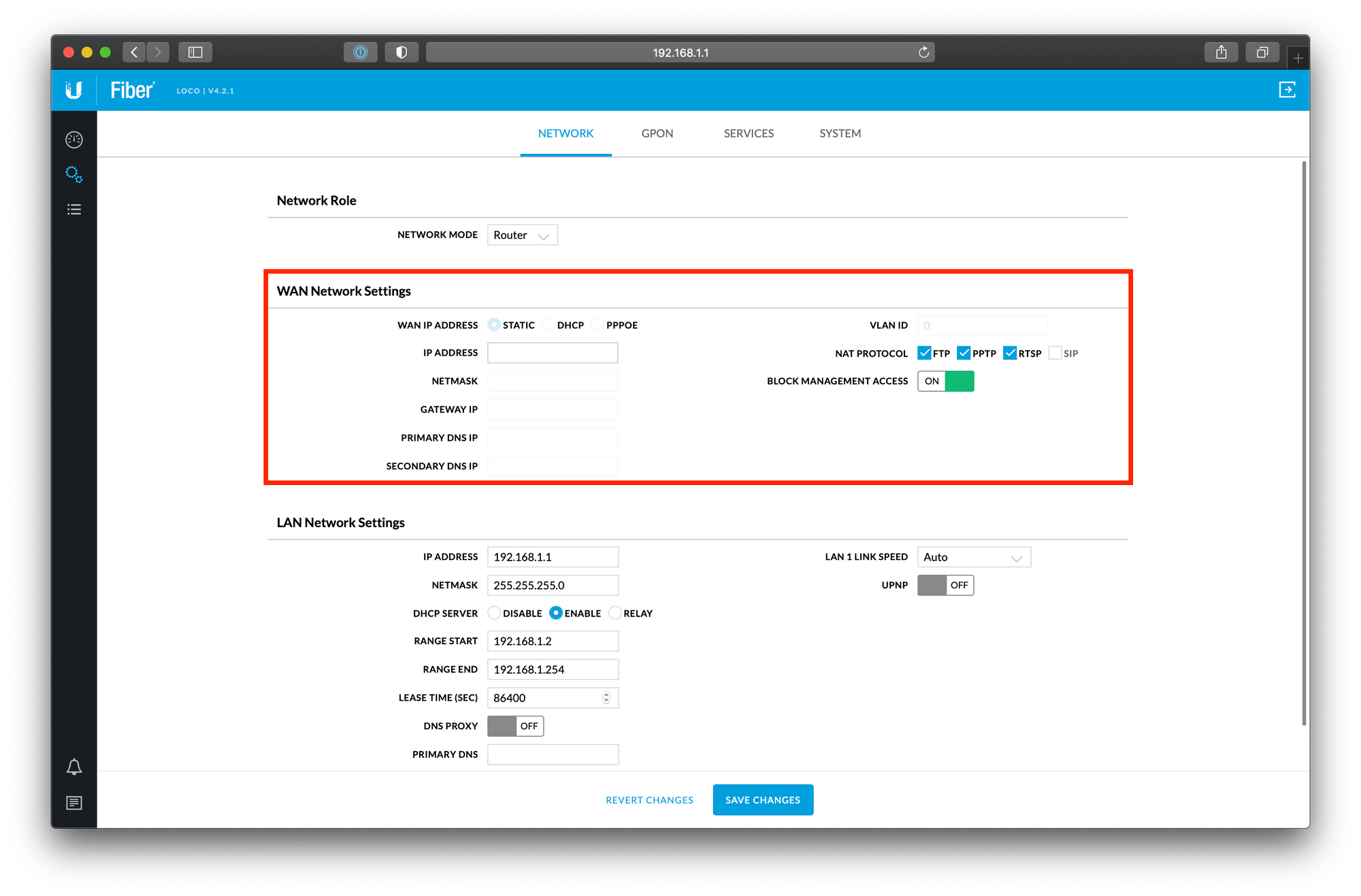
Configuring your modem involves a series of steps, including connecting it to your laptop or computer and setting up the network settings. These settings may differ depending on your internet service provider (ISP) and the type of modem you have. In general, though, the process often involves logging in to the modem's interface through a web browser and accessing the settings menu.
Once you're in the modem's settings menu, you'll be able to configure various settings, including the network name and password, as well as the type of internet connection you want to use. It's important to make sure these settings are correct, as they will determine how your modem connects to the internet and how your devices will connect to your network.
Additionally, some modems may require additional configuration for advanced features such as port forwarding or setting up a VPN. You will need to consult your modem's documentation or contact your ISP for assistance if needed.
Overall, configuring your modem can be a relatively simple process but it's important to do it correctly to ensure a steady and fast connection to the internet. If you're not confident in configuring your modem, don't hesitate to seek assistance from a professional or your ISP.