Network Traffic Control: Efficiently Managing Your Network Bandwidth
In today's digital age, fast and reliable network connectivity is more essential than ever. With the ever-increasing demand for network bandwidth, it is crucial to manage network traffic to optimize network performance. Network traffic control is the practice of prioritizing and regulating network traffic flow, ensuring that critical network applications run smoothly and efficiently. It involves controlling the usage of network bandwidth, reducing network congestion, and preventing bottlenecks from occurring.
One of the most effective ways of controlling network traffic is through Quality of Service (QoS) policies. QoS enables network administrators to assign different levels of priority to network traffic types, allowing them to optimize bandwidth for mission-critical applications. By ensuring that mission-critical traffic gets priority over non-critical traffic, network administrators can prevent network slowdowns and guarantee smooth network operation.
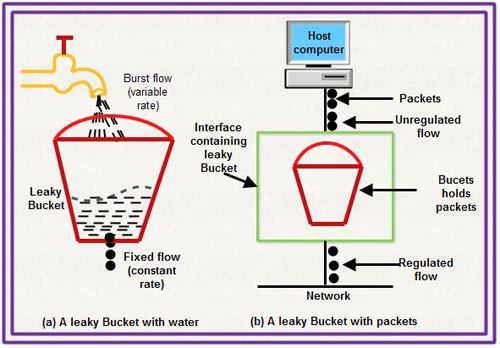
Another way of controlling network traffic is by implementing traffic shaping techniques. Traffic shaping involves regulating network traffic streams to ensure that traffic flows evenly and does not exceed network capacity. This can be done by prioritizing traffic based on the type of data involved, giving more throughput to certain types of data, and limiting the bandwidth of non-critical traffic streams.
Network traffic control also involves identifying and preventing attacks on network traffic. Implementing firewall policies and intrusion detection systems will help filter out malicious traffic, ensuring that your network resources are used only for legitimate purposes.
In conclusion, network traffic control is an essential aspect of network management. It enables administrators to optimize bandwidth usage, prevent network congestion, and ensure that mission-critical applications operate smoothly. By carefully managing network traffic, businesses can improve their productivity, reduce costs, and provide better service to their customers.