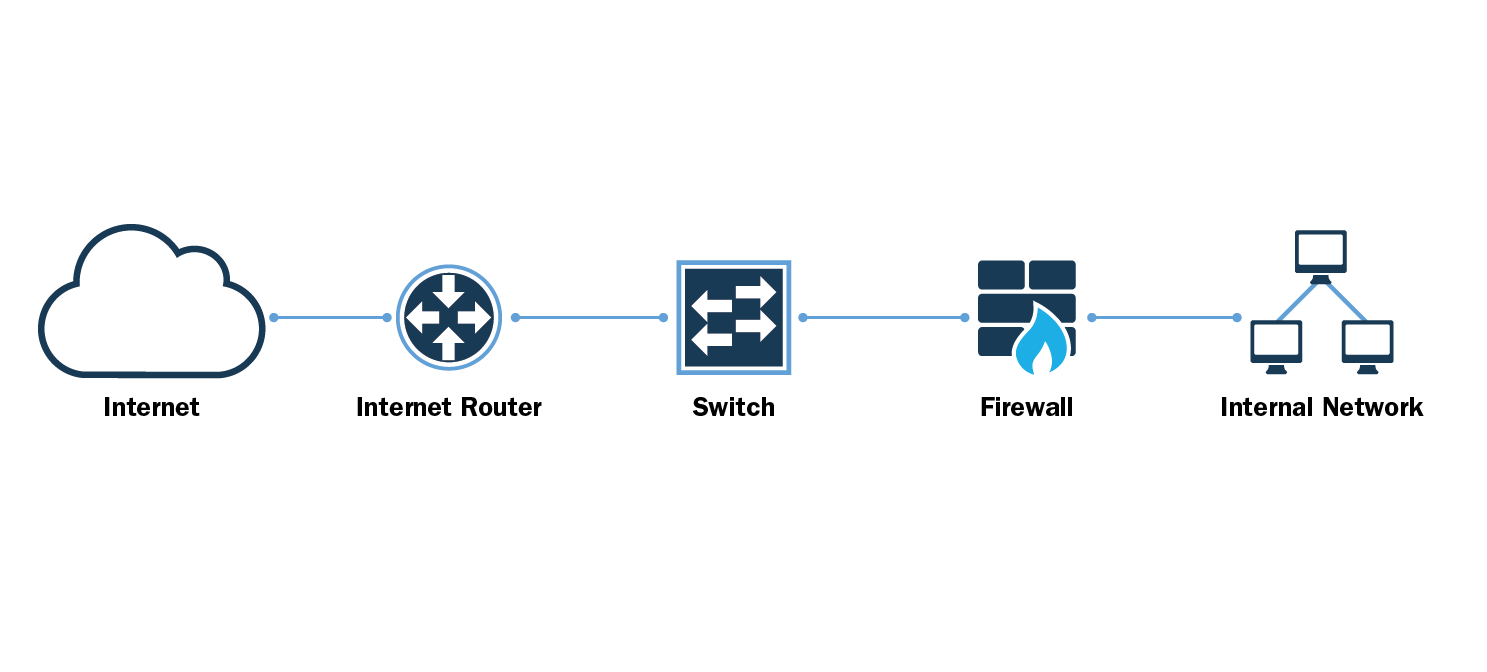
A VPN, short for virtual private network, is an essential tool that provides internet security and privacy. It is a private network that creates a secure and encrypted connection between your device and the VPN server through which it connects. VPNs are designed to provide various benefits for individuals and businesses alike.
Online security and privacy
One of the main reasons people use a VPN is to protect their online privacy as it encrypts everything you do online. A VPN ensures that your internet activity is concealed from hackers, snoopers, and other online criminals. It is particularly crucial when using public Wi-Fi, which can be easily hacked, putting your sensitive information at risk. A VPN ensures that your online identity remains anonymous, and your personal data remains safe.
Bypassing geo-restrictions
VPNs help users to bypass geo-restrictions, particularly for online streaming content. Many streaming services such as Netflix and Hulu are only available in certain countries or regions. By using a VPN, you can move your virtual location and access content that is not available in your region.
Access to business networks
VPNs are also an essential tool for remote workers accessing business networks. A VPN helps workers to protect sensitive data from prying eyes whenever they work outside a company's secured networks. VPN technology also enables them to access company files and data from remote locations safely.
Bottom line
VPNs are an essential tool that provides privacy, security, and accessibility while browsing the internet. It is a must-have for anyone who values their privacy, especially in today's online world, where hacking and data breaches are common occurrences. Whether you're a business owner or an individual, use a VPN to enhance your online security and make your online browsing experience safer and more private.