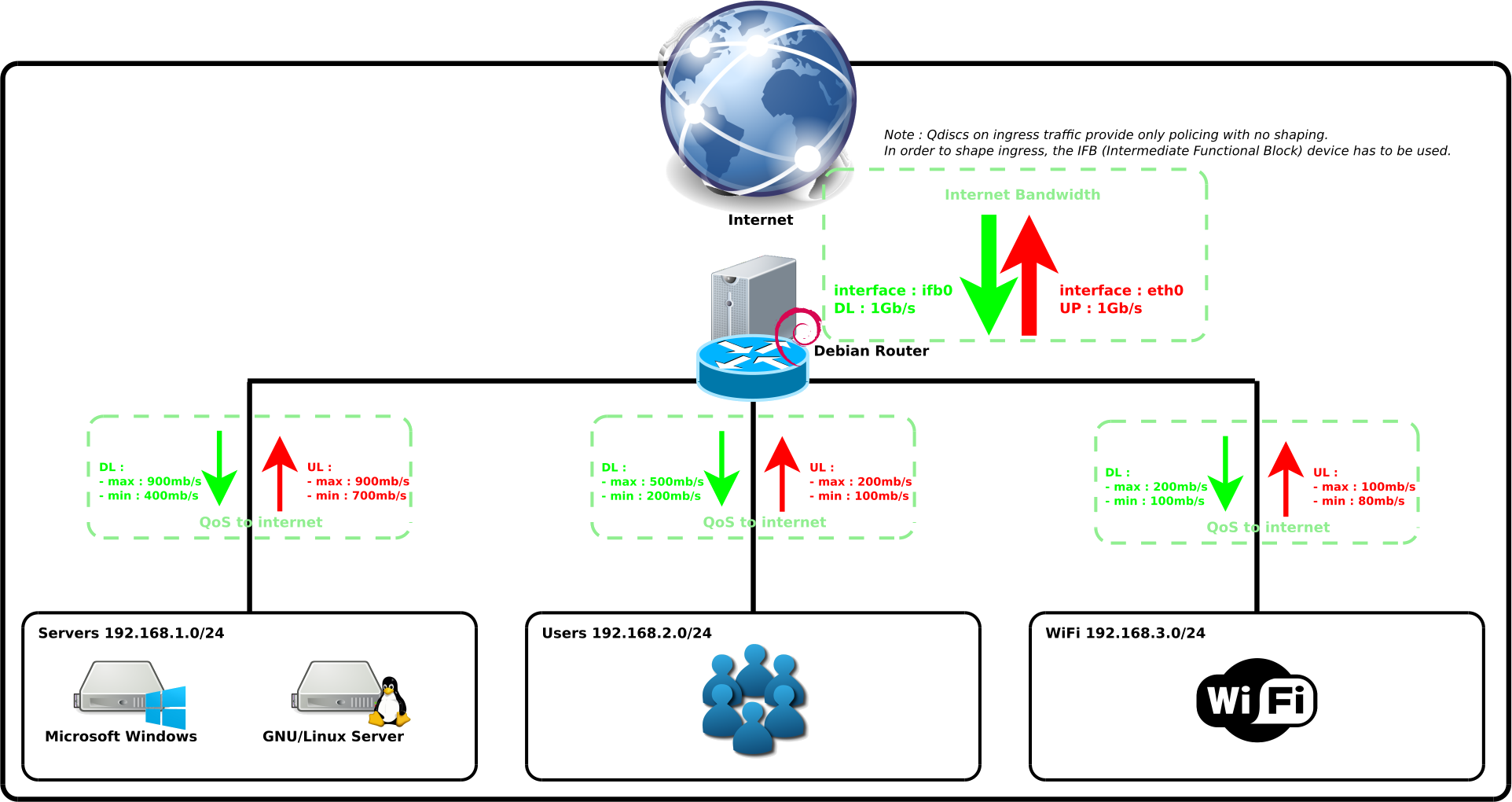
Network Quality of Service
As businesses and individuals rely more and more on internet-connected devices, the need for network quality of service (QoS) has become increasingly important. In a world where we expect lightning-fast internet speeds and reliable connections, network QoS ensures that data is transmitted efficiently and reliably.
Network QoS refers to the ability of a network to prioritize and manage the flow of data, ensuring that important packets are delivered quickly and efficiently while less important data is given lower priority. This is achieved through a complex set of technologies and protocols that work together to manage the flow of data on a network.
The benefits of network QoS are numerous, both for businesses and individuals. For businesses, network QoS ensures that critical applications and services are given priority, even during periods of high usage. This can lead to increased productivity, fewer delays, and better overall performance.
For individuals, network QoS ensures that streaming video content, online gaming, and other bandwidth-intensive activities are not interrupted by slower connection speeds or service interruptions. This can lead to a more enjoyable online experience and fewer frustrations.
Overall, network QoS is an essential component of any modern network, ensuring that data is transmitted efficiently and reliably. Whether you are a business owner or an individual, understanding the importance of network QoS can help you make informed decisions and get the most out of your internet-connected devices.