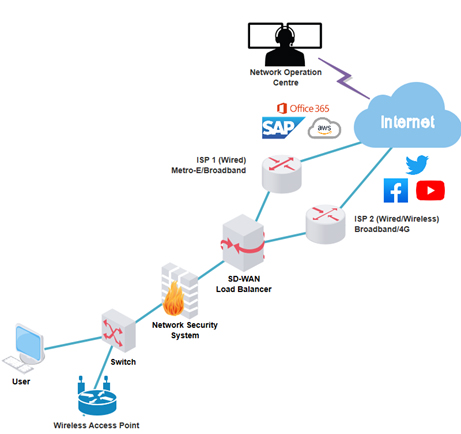
Network security implementation is a crucial and ongoing challenge for businesses in the digital age. With hackers constantly finding new ways to exploit vulnerabilities in networks, it's essential to stay up-to-date with the latest security measures and take a proactive approach to protecting your organization's sensitive data.
While many businesses may feel that their network is secure enough, the reality is that there is no such thing as absolute security. Even the most robust security measures can be circumvented by a determined hacker with enough time and resources.
That's why it's important to implement a multi-layered approach to network security. This may include a combination of firewalls, antivirus software, intrusion detection and prevention, data encryption, and employee training on best practices for network security.
Another important aspect of network security implementation is staying up-to-date with the latest threats and vulnerabilities. This may involve regularly conducting security audits or hiring outside experts to test your network for weaknesses.
Despite the challenges of network security, it's important not to become complacent. A security breach can have devastating consequences for a business, including loss of data, financial losses, and damage to the company's reputation.
Ultimately, investing in network security implementation is an investment in the long-term success and viability of your business. By taking a proactive approach to network security, you can protect your organization against potential threats and give yourself peace of mind knowing that your data is safe and secure.