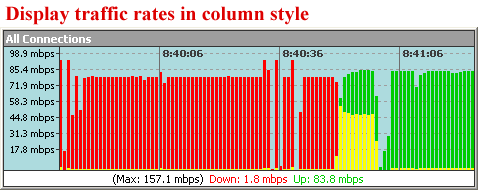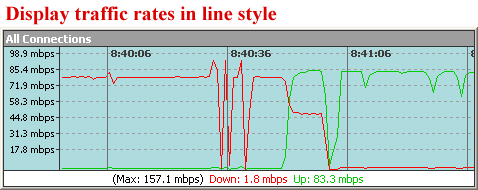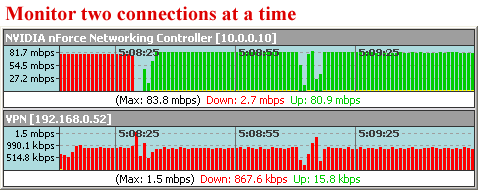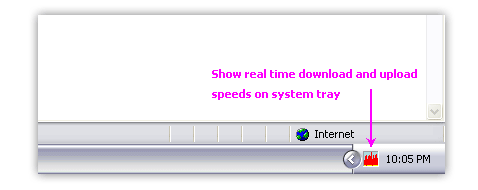
Firewalls are an essential element in today's Cybersecurity measures. They serve as a barrier between your computer network and the outside world. A firewall monitors and controls the incoming and outgoing traffic of your network to ensure that no unauthorized or harmful data can reach your system.
It acts as a filter that separates trusted networks from untrusted or potentially dangerous ones.
Firewalls can be hardware-based or software-based. Hardware firewalls are standalone devices and provide high levels of security as they are not exposed to the same vulnerabilities as software-based firewalls. Software-based firewalls, on the other hand, are installed on computers and offer a lower level of security.
Firewalls work in three layers, namely network, transport, and application layers. The network layer firewall works at the protocol level and monitors traffic based on the IP address and port numbers. The transport layer firewall works on the transport layer and monitors traffic based on sessions or conversations. The application layer firewall works at the application level and monitors traffic based on the specific applications being used.
Apart from their primary function of blocking harmful traffic, firewalls can also be used for many other purposes. They can help to improve network performance, prevent data leakage, and provide remote access for employees working offsite.
In conclusion, firewalls are an essential component for network security. They provide a critical layer of defense against cyber threats and unauthorized access. As cybercrime continues to grow in scope and scale, the importance of firewalls in securing networks can never be overstated.