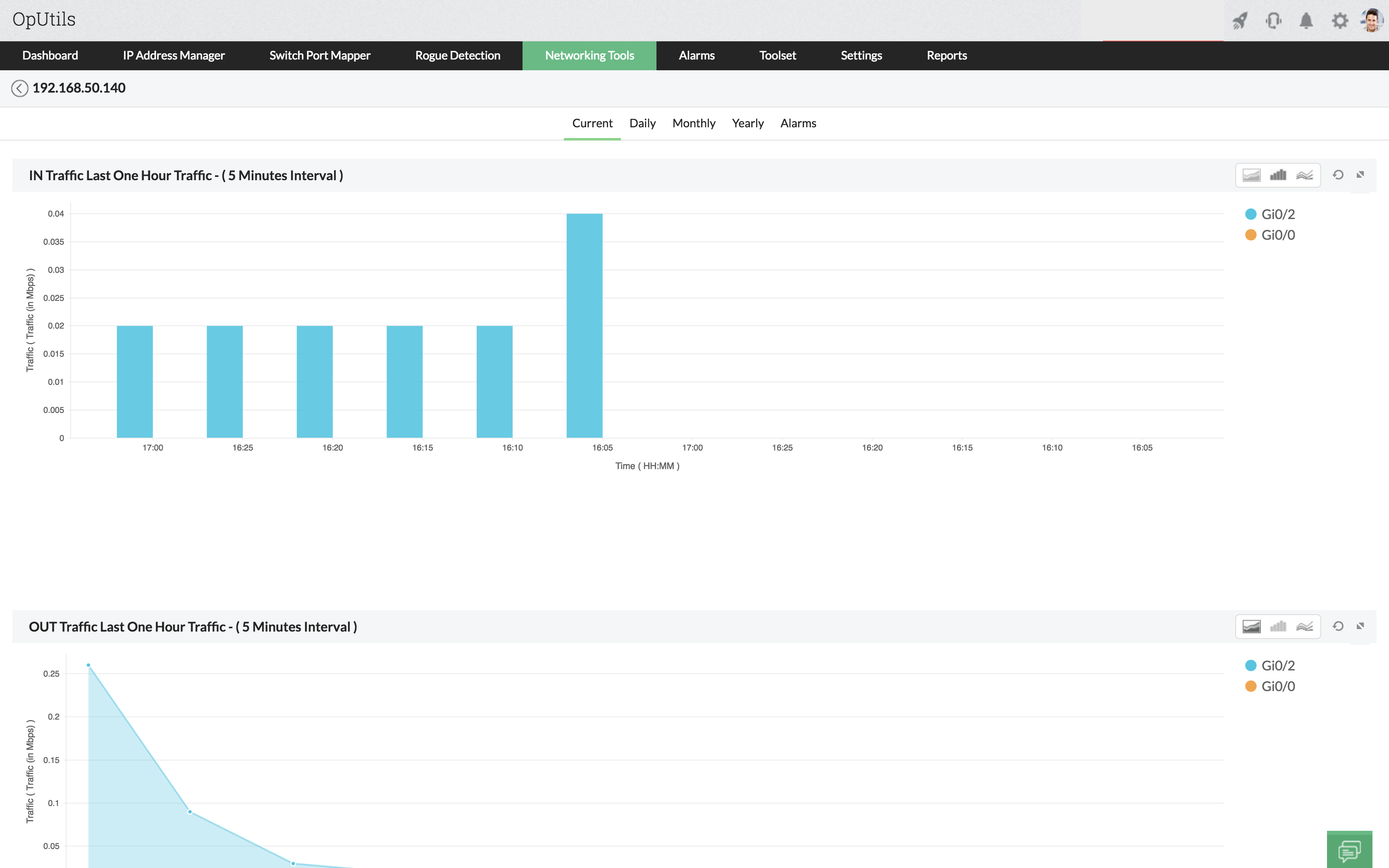
Are you seeking to optimize your network performance and improve your data analysis abilities? Look no further than a network traffic simulation tool, which can provide a comprehensive and accurate view of your network's activity.
Network traffic simulation tools offer a range of benefits, including the ability to predict potential network issues and critically analyze network data. By simulating network traffic, users can understand how data moves through their network and pinpoint areas for optimization.
Key Features
Most network traffic simulation tools offer a range of key features, including real-time monitoring, detailed reporting, and custom configuration options. With real-time monitoring, users can quickly identify network bottlenecks or other issues as they occur, enabling rapid problem resolution. Meanwhile, detailed reporting allows users to analyze their network data in-depth, revealing trends and patterns that can lead to network optimization.
Custom configuration options also give users the ability to tailor their simulation environment to their specific needs, simulating different network settings and scenarios to better understand how their network will behave and perform under different conditions.
Benefits
In addition to predicting potential network issues and critically analyzing network data, network traffic simulation tools offer several additional benefits. These tools can help users identify and resolve performance issues, proactively prevent network downtime, and ensure maximum network uptime. Additionally, by providing a comprehensive view of network activity, simulation tools make it easier for users to ensure compliance with industry regulations and standards.
Overall, a network traffic simulation tool can greatly enhance network performance and data analysis capabilities, helping users make better decisions and optimize their network for maximum uptime and reliability.