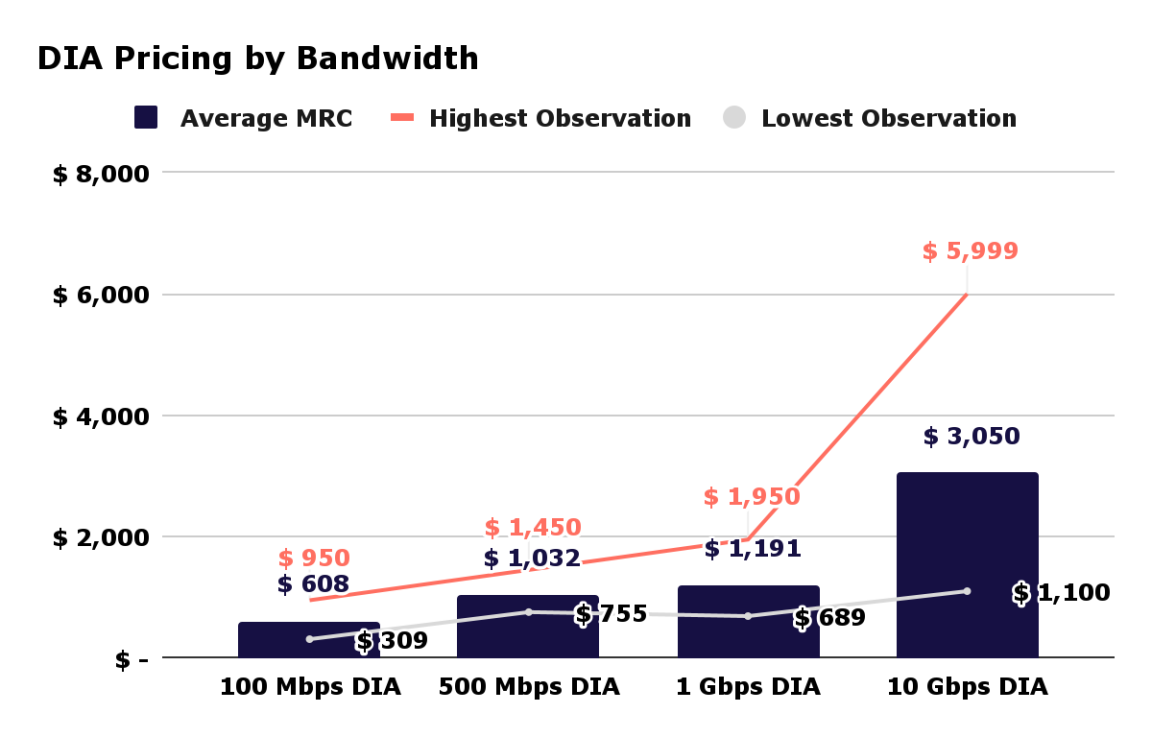
Router Settings Backup
Keeping a backup of your router settings is a smart move. In case of any accidental damage or loss of configuration, you can easily restore it to its previous state. Router settings backup is basically a copy of your router's configuration files that contains all the settings including: network type, name, password, and other specific settings.
There are different ways in which you can backup your router settings. Some routers have a “backup settings” function within their web interface which makes it easier to backup and automatically saves the settings in a file. Alternatively, you can manually save your router settings. For instance, you can save the configuration file to your local device, such as a computer or an external hard drive.
It is important to backup your router settings regularly, at least once a month depending on how often the settings are updated. This minimizes the risk of losing important data, and also saves you from the hassle of re-configuring your router from scratch.
Some users tend to switch routers frequently, and in such situations the backed-up settings come in handy. For instance, if you change your router for a better one, you can simply apply your previous configuration with little or no alteration.
In conclusion, router settings backup is crucial for the durability and functionality of your router. Make it a habit to backup your settings regularly, in order to preserve your data and avoid unnecessary stress.